Ivan on Containers, Kubernetes, and Backend Development
Hello friends!
It's Ivan Velichko, a software engineer and a technical storyteller, with my traditional monthly roundup.
I'd like to start this issue with the exciting personal news. I'm joining the Slim.AI team to build cool stuff for all of us dealing with containers.
I've been an old fan of the Slim.AI SaaS - a service where you can search images on multiple container registries simultaneously and inspect the image content right in the browser. I also admire the magic behind their OSS DockerSlim project - this tool can trim down a container image by some tens of percents without requiring much of the user input. And of course, there is a lot to come.
So, my innate interest in containers and solid ops experience made this role sound like a perfect opportunity - I'll be spending even more time tinkering with Docker and Kubernetes (meaning more insights on the blog and twitter 😉), and, hopefully, it'll result into something the whole DevOps guild could benefit from. Looking forward to my first day next week!
SPONSORED Kubernetes API Access Security Hardening - a worthwhile post by Teleport. Extremely relevant for those of us who's concerned with securing Kubernetes API access. Do recommend if you need to implement strong authN/authZ in Kubernetes clusters.
What I Was Working On
Somehow, this month I switched the gears from Kubernetes back to Containers. I'm not done with the Working With Kubernetes API series yet, and I still have at least three WiP articles - a "how to write a custom controller" primer, a client-go walkthrough, and a client-go "advanced stuff" article with the explanation of informers, work queues, and alike. But none of them were finished this month.
It all started from me running into this DockerSlim bug. While fixing it, I had to remember a few clever tricks:
April 3rd 2022
|
But after a week spent debugging containers, I couldn't already help but think of dumping my fresh Container thoughts to the blog:
- Learning Docker with Docker - Toying With DinD For Fun And Profit
- Cracking the Docker CLI: How to Grasp Container Management Commands
While preparing materials for one of these posts, I came up with a nasty technique - writing an entire Go program in a Dockerfile. It's obviously a very bad idea, especially for production use, but nevertheless, I shared it on Twitter, and it took off...
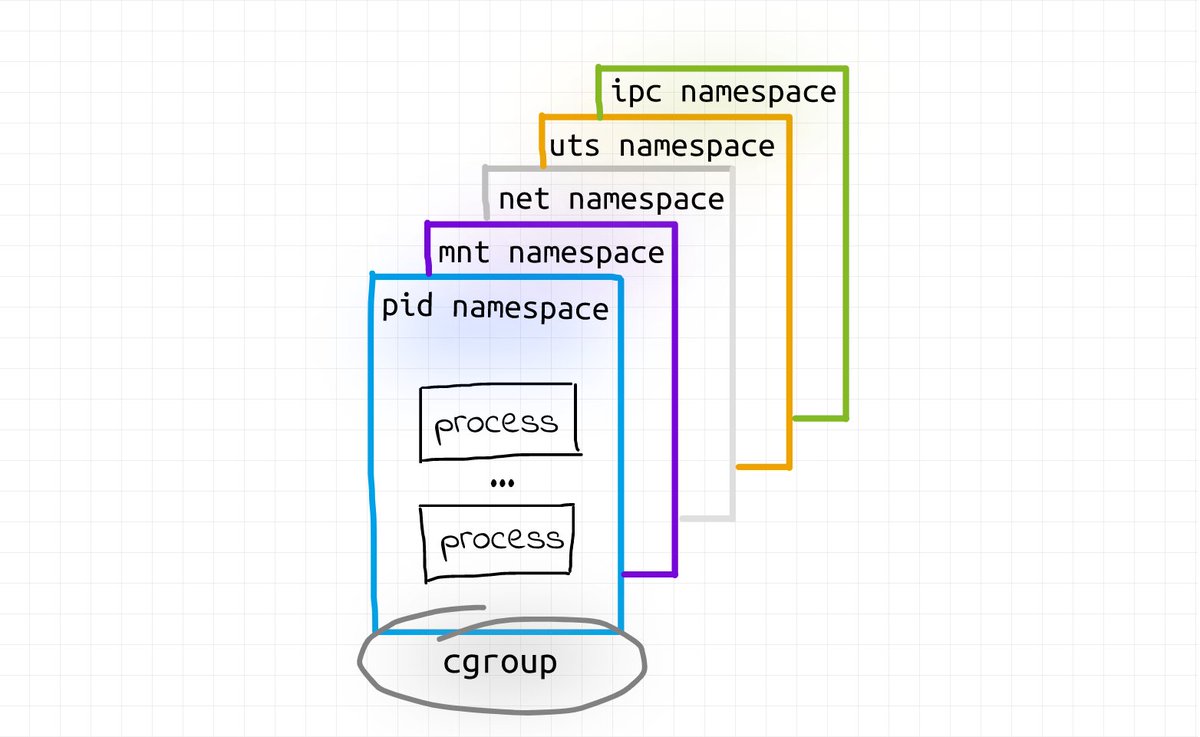
The above stuff took a surprisingly long time to write down, and by the end of the month, I felt bad that I didn't spend enough time working on my Kubernetes API series, so I ended up drawing this diagram on how to extend the Kubernetes API using Custom Resources, Admission Webhooks, and Controllers. Kind of a teaser of the future work:
What I Was Reading
- Running a Container off the Host /usr/ - Lennart Poettering, the creator of systemd, shares his thoughts on local development environments for folks doing system development. Pretty neat, but I'm still in favor of fully disposable playgrounds.
- Understanding root inside and outside a container - old but gold; there is still plenty of containers running as (true) root, and it's important to understand the difference.
- The shortcomings of rootless containers - kind of a follow-up for the previous article, but pay attention to the publication date - a lot might have been improved since then.
- The differences between Docker, containerd, CRI-O and runc - a good addition to my Journey From Containerization To Orchestration And Beyond.
- Limiting access to Kubernetes resources with RBAC - I wish this article existed when I'd been learning Kubernetes RBAC. It follows my favorite kind of explanation: start from a clear problem - how to do access control; show a technology-agnostic solution; map it to K8s primitives: Roles/RoleBindings/ClusterRoles, etc.
- Virtual Kubernetes clusters: A new model for multitenancy - for someone who spent the past few months developing a multi-cluster Kubernetes E2E testing framework, these virtual clusters sound very promising. Spinning up a bunch of KinD clusters on one machine is a pain.
- Kubernetes Ephemeral Container Security - "If there is one takeaway from this post, it is that any policy tool that has not been updated in the last couple of months will not enforce rules on ephemeral containers. This also includes all policies written in house! It is not enough to update the community policies." This is actually applicable to all Kubernetes features, not just ephemeral containers.
- The Principle of Ephemerality - the shorter, the better. This principle applies to almost everything in computing. Not just security credentials but also infrastructure. As a (former) Platform Engineer, I couldn't agree more.
- How Go Mitigates Supply Chain Attacks - hot topic for everyone these days...
- containerd CRI plugin: Insecure handling of image volumes - please upgrade your clusters.
- Introducing Dagger: a new way to create CI/CD pipelines - Dagger is out ❤️ From my experience, CI/CD still sucks in 2022. Hopefully, Dagger will do the same to CI/CD that Docker did to Containers.
- Merkle Trees - this data structure (?) became (in)famous with the rise of crypto, but Matt Rickard kindly reminds us that it's been used in many other places too. Kudos to Matt.
- An incredible story on protecting replit from hackers - this is nuts! But I'm particularly interested in stories like that because I still haven't given up on the idea of turning my blog into an interactive learning platform one day.
Stay Tuned
Well, this is it for this month. A lot of stuff, but even more to come! Stay safe and healthy, friends! And make code, not war!
Cheers,
Ivan Velichko
P.S. If you find this newsletter helpful, please spread the word - forward this email to your friend :)
Ivan Velichko
Building labs.iximiuz.com - a place to help you learn Containers and Kubernetes the fun way 🚀
Hey there 👋 I spent a few weeks deep diving into cgroup v2, and I'm happy to share my findings with you! Everyone knows that Docker and Kubernetes use cgroups to limit the resources of containers and Pods. But did you know that it's very easy to run an arbitrary Linux process in a cgroup using much more basic tools? The only kernel's interface for cgroups is the virtual filesystem called cgroupfs typically mounted at /sys/fs/cgroup. Creating folders there and writing to files in them is...
Hello friends! Ivan's here with the June roundup of all things Linux, Containers, Kubernetes, and Server-Side craft 🧙 What I was working on The first two lessons (and a few challenges) of my "Alternative Introduction to Dagger" course have not sparked much interest among my students, so I had to put this work on pause. With a heavy heart, though, because I do like Dagger, and I was enjoying working on the content about it. But no interest means fewer iximiuz Labs Premium subscribers, and I...
Hello friends! It's time for my traditional monthly roundup of all things Linux, Containers, Kubernetes, and Server-Side craft 🧙 Before we get started, I want you to know that this newsletter's previous issue (dispatched mid-May) was delivered to only about 1/5th of my usual email audience due to an unfortunate DNS misconfiguration. The good news is that you can still find it and all previous issues on newsletter.iximiuz.com. Also, if you reply to this email, it'd help to restore the domain's...